Introduction
The objective of this project was to create a compact and covert penetration testing tool capable of identifying vulnerabilities in IoT devices and safeguarding networks against unseen threats. Using a Raspberry Pi 3 Model B+, paired with PiRogue OS, Suricata, and Grafana, I developed a remote IoT pentesting platform equipped with powerful capabilities.

Tools and Technologies
This project leveraged PiRogue OS, a custom operating system developed by Defensive Lab Agency, preloaded with tools designed for network analysis and intrusion detection.
Features of PiRogue OS:
- Network Traffic Analysis:
- tcpdump: Captures network traffic into PCAP files.
- mitmproxy: Intercepts and logs HTTPS traffic.
- Intrusion Detection:
- Suricata: Detects malicious traffic based on rules.
- nfstream: Inspects traffic flows to identify applications.
- Device Forensics (not in this project’s scope):
- adb: Interacts with Android devices.
- libimobiledevice: Interfaces with iOS devices.
- MVT: Conducts device forensic analysis.
- frida: Runs programs on devices for instrumentation.

Data Visualization
Data visualization was achieved using the following tools:
- influxdb: Stores data generated by nfstream and Suricata.
- Chronograf: Enables searching and exporting data stored in influxdb.
- Grafana: Provides dashboards for visualizing network activity.
This setup offered actionable insights into the network's vulnerabilities through intuitive and dynamic visualizations.
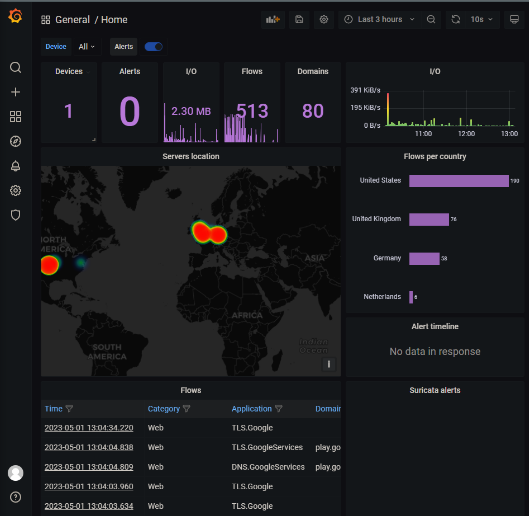
Workflow and Features
A highlight of PiRogue OS is its preconfigured integration of tools, simplifying the setup. The CLI dashboard, accessed via pirogue-ctl status, provides a centralized overview of the system's status and activity.
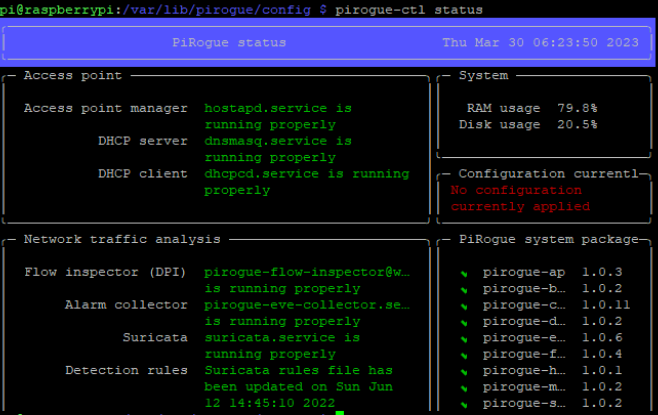
Tools Focused on in This Project:
- tcpdump, mitmdump, and mitmproxy: For network traffic analysis and HTTPS interception.
- Suricata: For real-time intrusion detection.
- influxdb and Grafana: For storing and visualizing collected data.
Challenges and Limitations
While the platform demonstrated potential, it was constrained by the hardware limitations of the Raspberry Pi 3 Model B+:
- Limited RAM: Struggled to handle multiple resource-intensive tools.
- Performance Issues: Prolonged execution times and sluggish system responsiveness.
Positive Takeaways
Despite the constraints, the project showcased several strengths:
- Streamlined Integration: Tools like Grafana and influxdb worked seamlessly, demonstrating the platform’s potential for network monitoring.
- User-Friendly Experience: Preconfigured tools provided an intuitive user experience, even under resource limitations.
Future Plans
To address the limitations, I plan to revisit the project using a Raspberry Pi 4, which offers:
- Increased RAM for better multitasking.
- Improved processing power to handle resource-intensive tasks.
This upgrade will likely unlock the full potential of PiRogue OS, making it a practical tool for real-world network intrusion detection and security testing.
Conclusion
This project served as a valuable learning experience, combining theoretical knowledge with practical application to build a remote IoT pentesting platform. Although hardware constraints posed challenges, the insights gained pave the way for future improvements.
With a more powerful platform, this project has the potential to become a robust and efficient solution for securing IoT networks.
Sources: